Inspect all encrypted traffic made from your iPhone
And there is a way to actually see every request being made from your phone. This means you will see both traffic made from each of your app, and your browser etc.

Overview
A lot of people use their smartphone every day without having a single clue about what data actually leaves their phone and what gets sent back to it. I mean, because you can't see something inside the app doesn't mean the app doesn't send it. There's a lot of data the user never sees. And there is a way to actually see every request being made from your phone. This means you will see both traffic made from each of your app, and your browser etc. Even the traffic the phone itself sends when you wake the device. I think there are many reasons for which you might want to see this traffic:
- You want to learn how other apps are built. For inspirational purposes.
- You're curious how other developers design their API's.
- You want to find vulnerabilities before others do.
- Realize that what your app does is not that "hidden" from the outside world - anyone can inspect their own phone and see all your encrypted traffic.
- You want to see what happens each time you open the app, and each time you close it. Some apps for example sends your positional data every single time you just open the app.
To do this kind of inspection is where proxy comes in. You essentially do a man-in-the-middle (mitm) attack on yourself.
In this post I will explain how to do it with MacOS, Charles Proxy, and an iPhone. Technically speaking you can do the same with Android or any other phone. I've done it before with Windows and Fiddler.
So what you need:
- MacOS
- Charles Proxy
- your iPhone
How to proxy your iPhone traffic through Charles Proxy
- Install Charles Proxy on your mac by either downloading from https://www.charlesproxy.com/documentation/installation/ or install with
brew cask install charlesif you prefer brew. - Make sure you don't already have a proxy configured on your iPhone. Could either be manually or some VPN app running.
- Install the Charles root certificate on your mac by following the MacOS section in this guide (needed to inspect encrypted traffic): https://www.charlesproxy.com/documentation/using-charles/ssl-certificates/
- Install the Charles root certificate on your iPhone by following the iOS section in this same guide (needed to inspect encrypted traffic): https://www.charlesproxy.com/documentation/using-charles/ssl-certificates/
You must use the Safari browser to install this root certificate I think. You can use your browser of choice later on when everything is set up. - Start Charles Proxy on your mac if you haven't yet.
- Follow the guide here to connect your iPhone to Charles: https://www.charlesproxy.com/documentation/faqs/using-charles-from-an-iphone/
The first time Charles will prompt you on your mac to allow this device to be inspected. - You're good to go - now all your traffic from your iPhone should be seen inside Charles Proxy on your mac! Both non-SSL (unencrypted) traffic and SSL (encrypted) traffic made by any app or browser from your iPhone. So just open your favorite app and watch Charles show you all the requests.
Real world example 1 - my blog
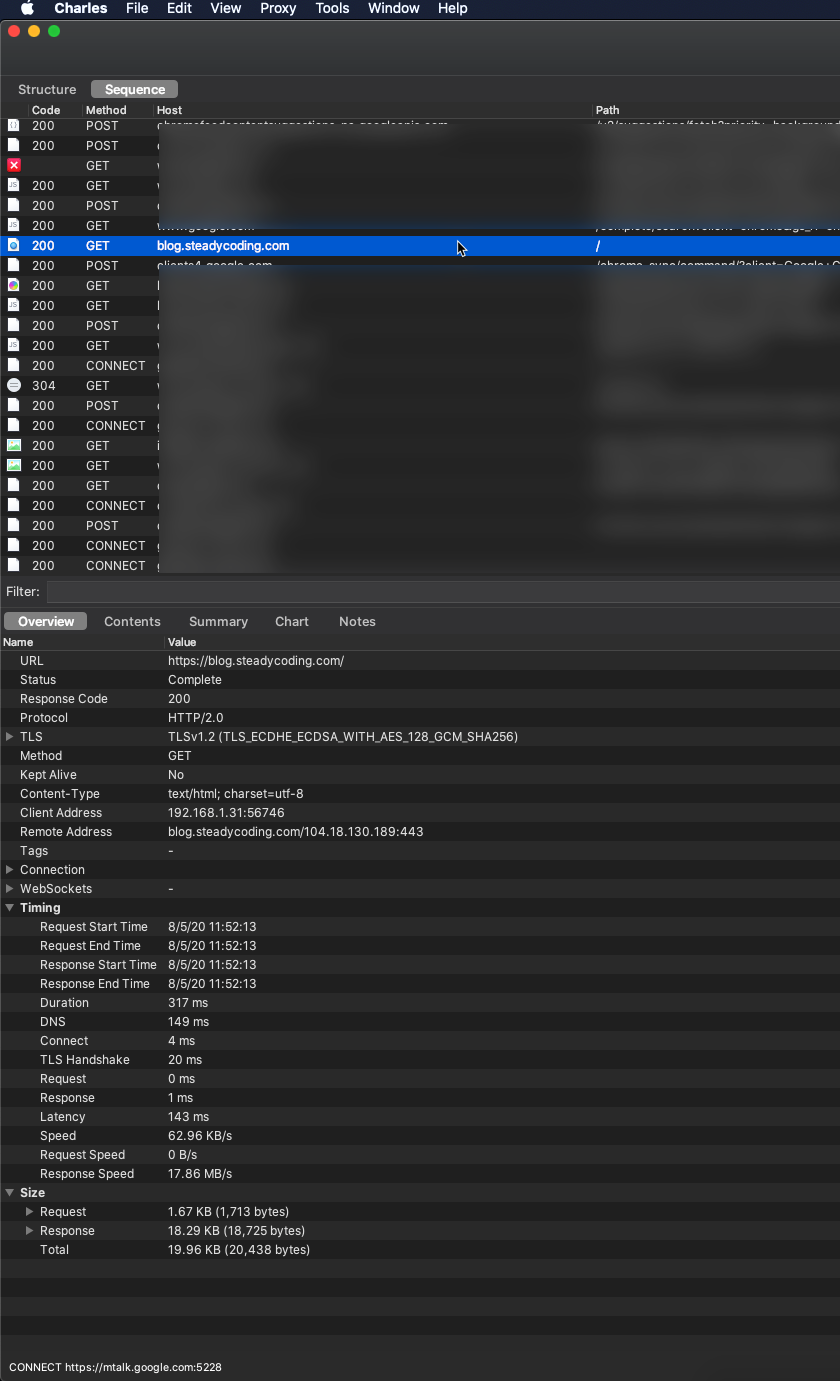
When I open Chrome on my iPhone, go to https://blog.steadycoding.com/, then it will show up in Charles on my mac. Not too exiting here, since this will give me a static page, but you can see the host, path, http method, TLS protocol, contents of the request/response etc. This is pretty neat, and a good start. I've blurred everything else as you can see, for obvious reasons, but there's a lot of different requests to inspect here.
The top section is all requests and the bottom section is all data for that specific request marked in blue.
Real world example 2 - food delivery (yikes!)
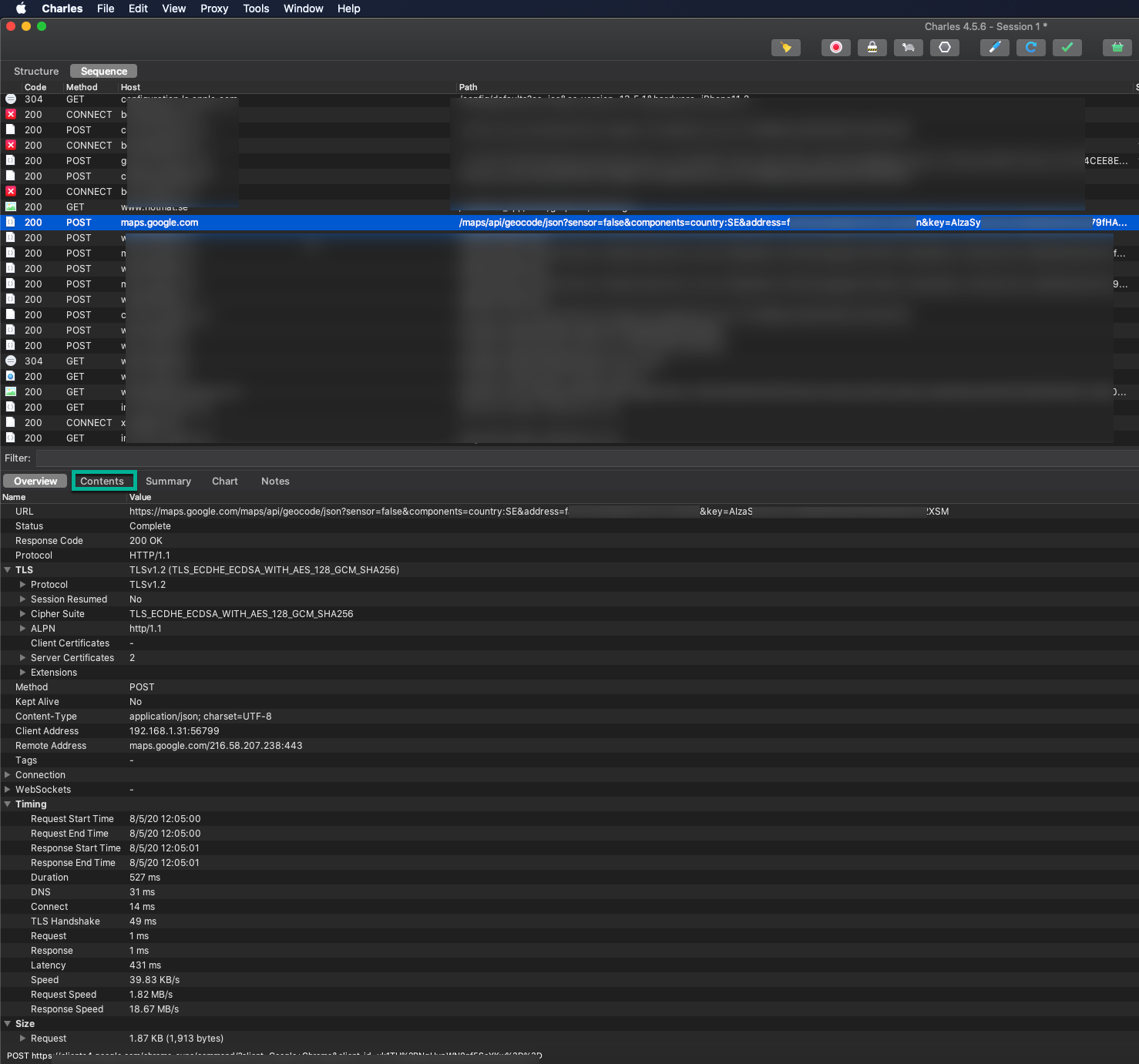
I opened an app I can use for home delivery of food. When I want to order food I must enter my address. Now I can see in Charles Proxy that the app itself is then sending that address with a POST request to maps.google.com to find addresses matching my search term.
The interesting thing here is that there is an API key as a query string parameter. Not sure this was the developers intention - to "expose" the API key for Google Maps here. I've blurred it for obvious reasons, but this API key could be used against them. Maybe there's a cost associated with how many requests that API key has made during a month for example.
If you click the "contents" tab marked in green you can see the actual request data sent and received too. That'll be up to you to go there and look.
Summary
Pretty short post I know - but to be honest I think this is all you need to get started. What app you decide to inspect or what sites are up to you.
There's a lot of power with using a proxy for cases like this. Of course you'll just see your own traffic - it's not like your inspecting other peoples traffic - but still it's powerful to see how other apps are written.
